OneDesk allows you to set up single sign-on (SSO) to permit your users to log in using their existing credentials. If the user does not exist, once they log in using SSO, OneDesk will create a user record for them. Since email addresses must be unique in OneDesk, it is important that you do not already have a customer record with the user’s email address or the sign on will fail. OneDesk supports both OpenID and SAML protocols.
Enable and Configure SSO for Users in your OneDesk account
SSO requires the Enterprise level plan of OneDesk
The basic steps to enabling SSO for your users in OneDesk are as follows:
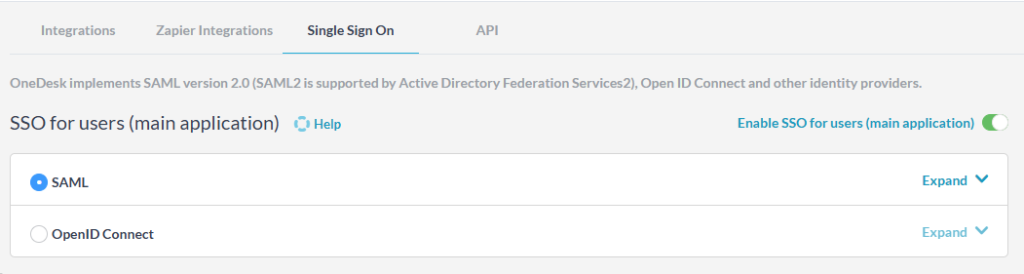
- Go to: Administration > Integrations > Single Sign On
- Turn on the switch “Enable SSO for Users”
- Select ‘OpenID Connect’ or ‘SAML’
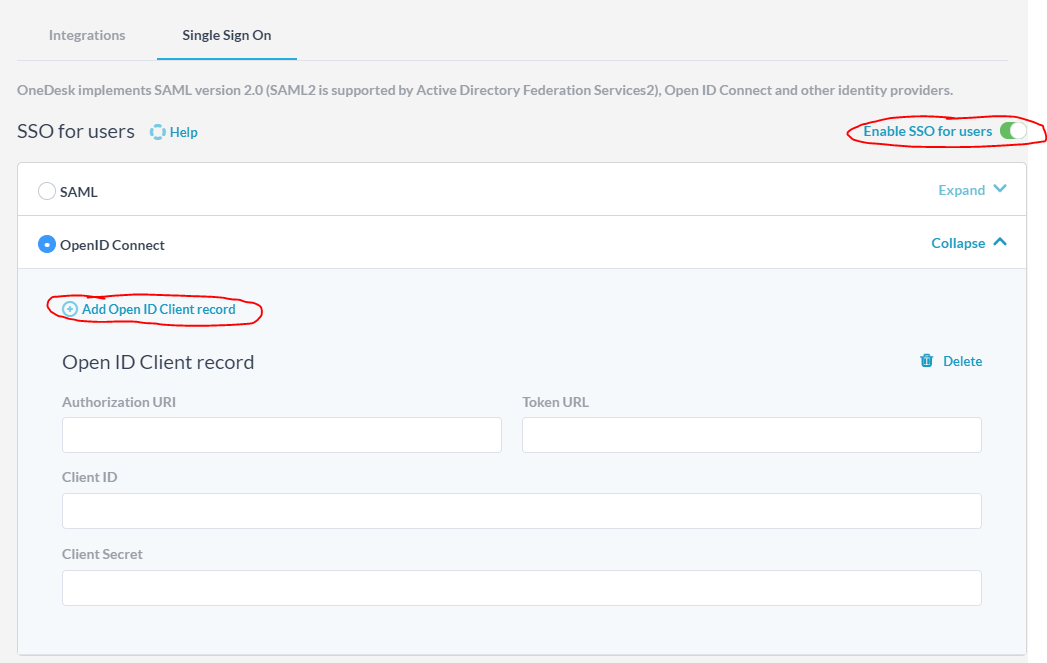
- For OpenID, click “Add Open ID Client Record”, then complete the required fields for Authorization URI, Token URL, Client ID, and Client Secret.
- For SAML, you will need to copy your ACS URL and Entity ID and provide it to your IdP. Then provide OneDesk your Entity ID. from your IdP.
- When completed, use the generated URLs to automatically log your users into the main web app.
Example Single Sign-On using Microsoft Azure Active Directory (Open ID)
1. Add Open ID Client Record
- Go to: Administration > Integrations > Single Sign On.
- Toggle on ‘Enable SSO for users.’
- Select and expand ‘OpenID Connect’, and click ‘Add Open ID Client record’.
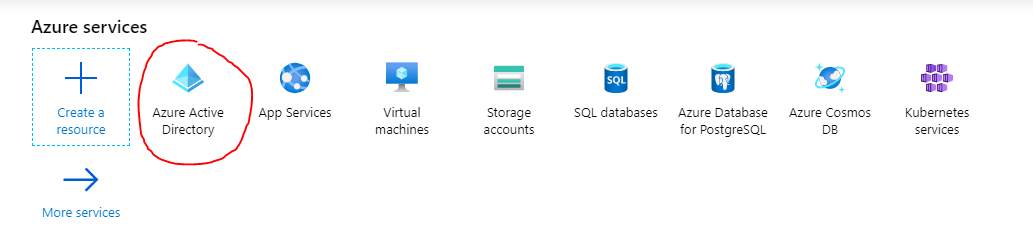
2. In Azure, create a new App Registration
- In Azure, open ‘Azure Active Directory’.
- Select ‘App Registrations’ and click ‘New registration’.
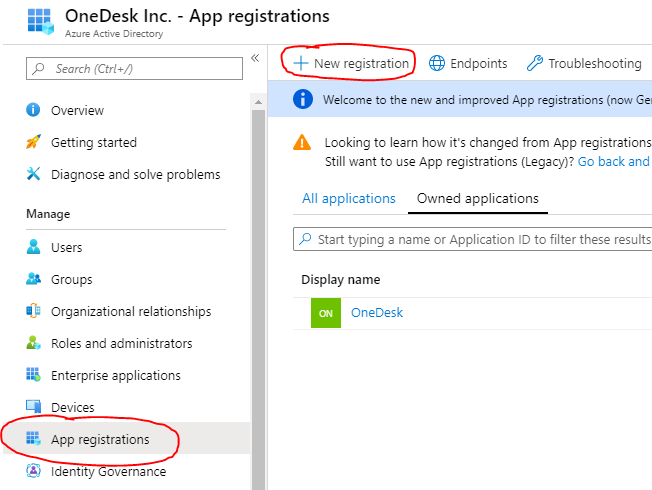
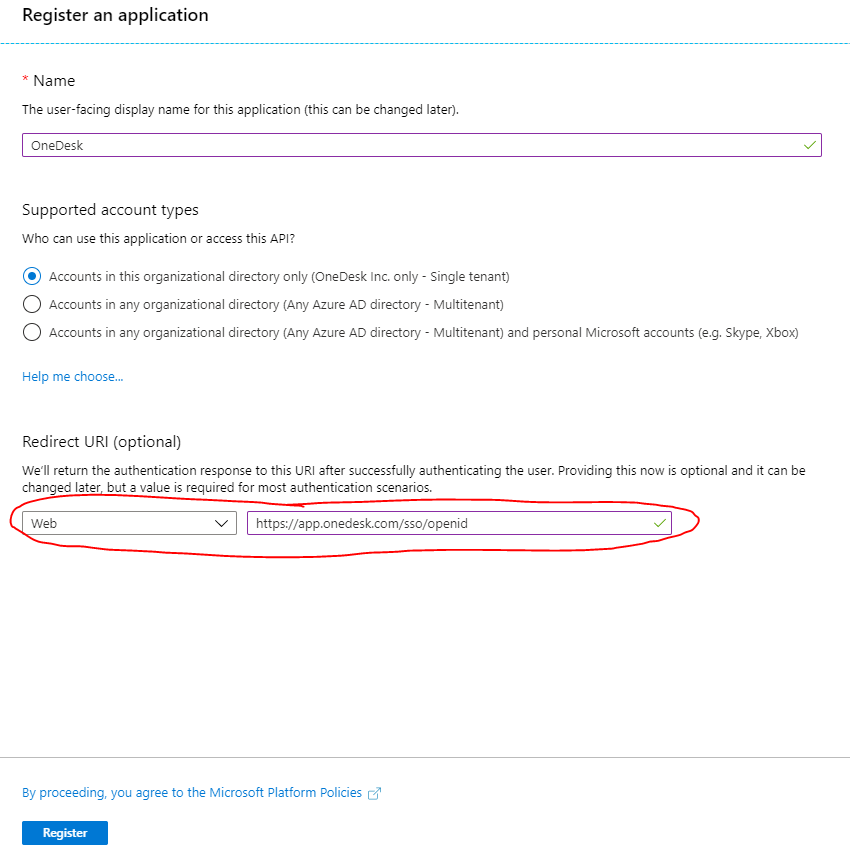
Register the OneDesk application by:
- Giving it a name: ‘OneDesk’.
- Adding the Redirect URI as: ‘https://app.onedesk.com/sso/openid’.
- Clicking ‘Register’.
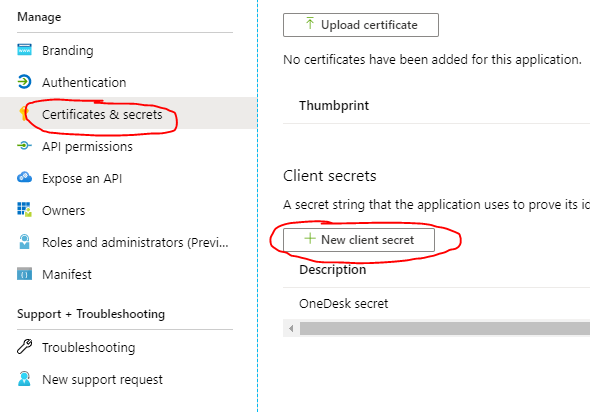
3. Create and copy over a ‘Client Secret’
- Click ‘Certificates and Secrets’.
- Click ‘New Client Secret’.
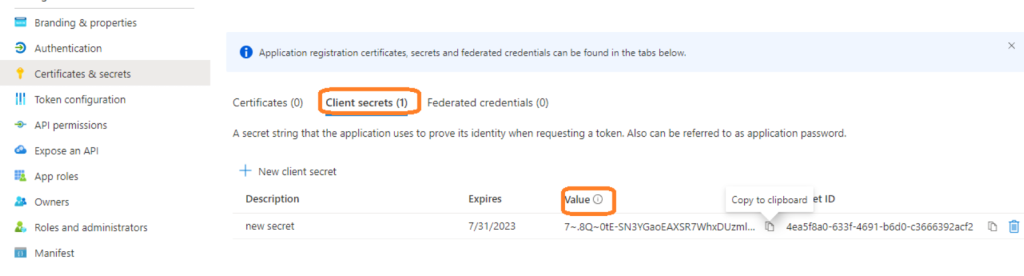
- Copy the Client Secret Value over to the ‘Client Secret’ field in OneDesk.
Note: Make note of the client secret expiry date. If the secret expires, your SSO will stop working.
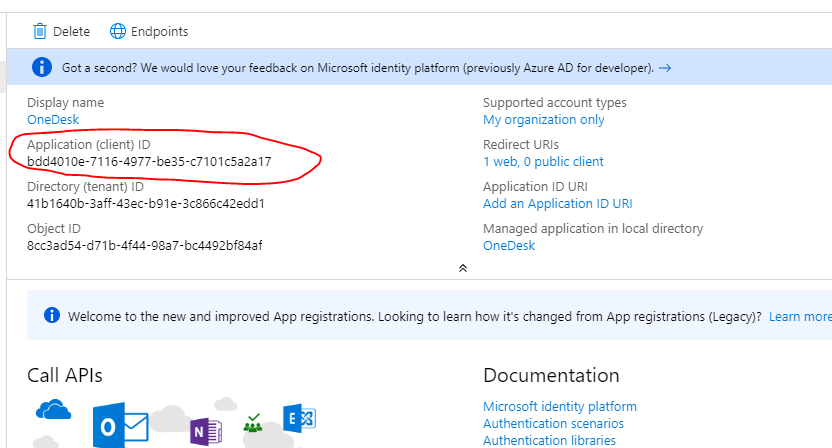
4. Copy over the ‘Client ID’
- In Azure, in the the newly registered app (called ‘OneDesk’), copy the ‘Application (client) ID’
- Paste it into the ‘Client ID’ field in OneDesk
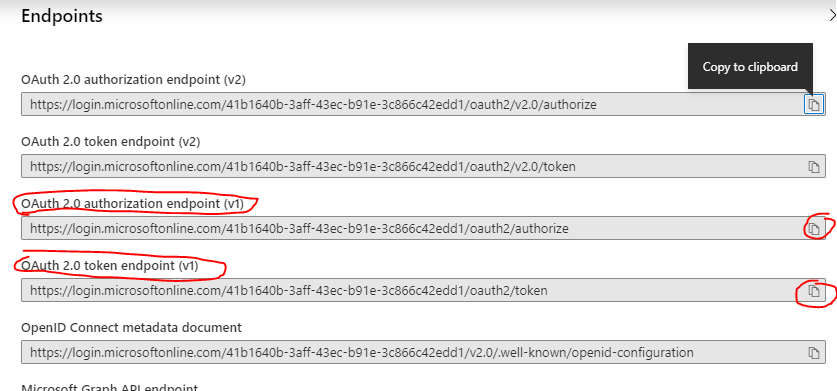
5. Copy the Endpoints to ‘Authorization URI’ and ‘Token URL’
- In Azure, in the the newly registered app (called ‘OneDesk’), click the ‘Endpoints’ button.
- Copy the ‘OAuth 2.0 authorization endpoint (v1)‘ to the ‘Authorization URI’ field in OneDesk.
- Copy the ‘OAuth 2.0 token endpoint (v1)‘ to the ‘Token URL’ field in OneDesk.
6. Here is the completed OpenID Client record in OneDesk
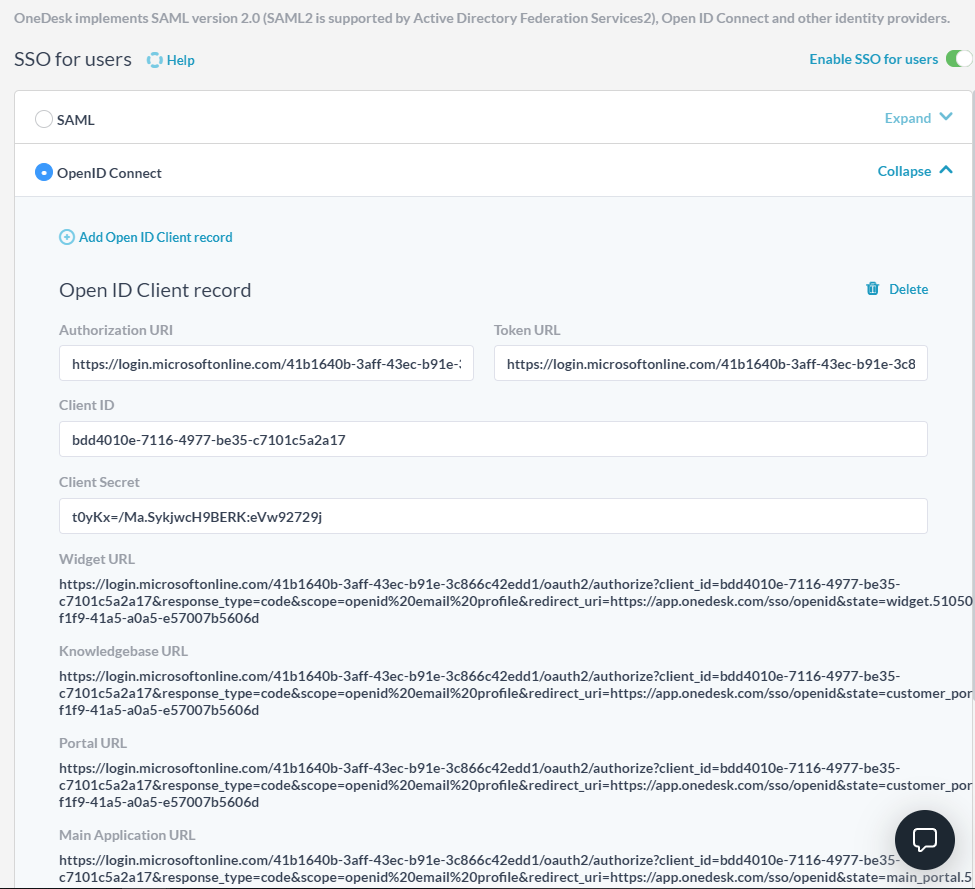
Use the provided URLs to log into OneDesk
As soon as the record is completed, OneDesk will generate a list of URLs, one for each of your Customer Apps. Use the appropriate URL to allow your customers to log into that customer app using their Azure Active Directory credentials. You will probably primarily want to use the ‘Main App’ URL, however, by default OneDesk also generates URLs for the website widget (for live chat and more), for the Customer Portal, and for the knowledgebase. Use them as necessary.
Watch a video
Here is a video of enabling SSO for OneDesk using Microsoft Azure Active Directory.
Troubleshooting – SSO is not, or has stopped working
- Make sure the client secret has not expired. During initial set-up of SSO, you are prompted to select an expiry date for your client secret. The expiry date can be customized, but it is always necessary to set an expiry. If your SSO has stopped work, ensure your client secret has not expired. If it has expired, the connection will need to be reset.
- Disable SSO and try again. Disabling/disconnecting your SSO and connecting again often fixes the issue.
- Screenshot the error message. Send us a screenshot of the error message your are receiving.